Symbol code red virus 227714
When this replication succeeds, the affected areas are then said to be infectedCode Red and Code Red II are both worms, which are attacks that propagate themselves through networks without any user intervention or interaction Both take advantage of a flaw in a component of versions 40 and 50 of Microsoft's⚠️ Warning Emoji Meaning A triangle with an exclamation mark inside, used as a warning or alert Warning was approved as part of Unicode 40 in 03 under the name "Warning Sign" and added to Emoji 10 in 15 Copy and Paste

9 Types Of Malware And How To Recognize Them Cso Online
Symbol code red virus
Symbol code red virus-Zachery Mitcham, Director of Network Services at New Hanover Regional Medical Center discusses their protection against Code Red Virus with WECTTV NewsCode red is a computer worm that was identified in July 01, when computers running on Internet Information Services (IIS) web server of Microsoft were found compromised The after effect of the attack caused a damage of billions of dollars in the summer of 01




Vector Red Stoppage Sign With White Virus Inside And Black Inscription Royalty Free Cliparts Vectors And Stock Illustration Image
Code red is not easy to remove which is quite annoying as it never does anything serious to your computer, but it can be removed by a specialist Who created CODE RED?Friendly This character has no intent to harm the computer, only to help it They most likely live here Unknown This character doesn't seem to want to harm or help the computer A visitor, maybe?Symbol Scanners have gained a reputation for reliability, durability, and affordability Symbol offers barcode scanners with a rugged design for the warehouse or a general purpose scanner for the retail point of sale Their patented scanning technology allows for both 1D and 2D barcodes to be scanned and read Symbol's top barcode scanners include the LS28, LS3578, and DS6708
Corruption This character seeks to kill, manipulateMoved Permanently The document has moved hereThe symbolism of the color red Red Cross The Red Cross on white background was the original protection symbol declared at the 1864 Geneva Convention Red star The fivepointed red star is a symbol of communism as well as broader socialism in general
GLOSSARY OF SYMBOLS SYMBOL STANDARD REFERENCE STANDARD TITLE SYMBOL TITLE EXPLANATORY TEXT EN 980, Clause 512 Symbols for use in the labelling of medical devices Manufacturer Indicates the medical device manufacturer ISO , Clause 511 Medical devices — Symbols to be used with medical device labels, labelling and information to be suppliedTwo Days in the Life of a Worm On , more than 359,000 computers were infected with the Code Red worm in less than 14 hours, says David Moore of the Cooperative Association forVirus Code Red raised Published 1 year ago on 17 AM By Elmer Navarro Manuel @tribunephl_lmer DOH Secretary Francisco Duque gives an update as a code red sublevel alert was issued yesterday following the fifth person that tested positive for COVID19 in the country PHOTOGRAPH BY BOB DUNGO JR




Bug Shaped Computer Virus Infecting Lines Of Code Stock Photos Freeimages Com




Red Binary Code Background Computer Problems Concept Black Stock Photo Picture And Royalty Free Image Image
Any link to or advocacy of virus, spyware, malware, or phishing sites A simple solution would be to insert the symbols and format with the red colour and the size you use most Then select and save as formatted autocorrect entries for #c (clubs) #h (hearts) etc Type #h to insert a red heart symbol Any other inappropriate content orThe Department of Health on Saturday raised its alert system for coronavirus disease 19 (COVID19) to Code Red after it confirmed the first case of localized transmission of the deadly infectionAugust 4 A complete rewrite of the Code Red worm, Code Red II begins aggressively spreading onto Microsoft systems, primarily in China September 18 The Nimda worm is discovered and spreads through a variety of means including vulnerabilities in Microsoft Windows and backdoors left by Code Red II and Sadmind worm




Virus Bug Code Skull Design Vector Art At Vecteezy




Virus Lilly Lounge Apr 17 15 10 00pm
>>Code type in notepad @echo off shutdown r f t 00 Form Of Switchess Shuts down the PCl Logs off the current usert nn Indicates the duration ofHTML character codes All HTML character codes of text fonts and symbols from �Click on character to get HTML code



Code Red Virus Archives Mirekusoft Install Monitor The Smart Approach For A Fast And Clean Pc




What Is Malware Definition And How To Tell If You Re Infected Malwarebytes
Salah satu contoh dari worm adalah Code Red Code Red merupakan worm yang dapat mengeksploitasi lubang keamanan di Microsoft Internet Information Server (IIS) untuk menyebar Seperti lazimnya virus, cacing Code Red dapat berkembang biak menjalar dari komputer ke komputer lainDescription This vulnerability could allow an attacker, from a remote location, to gain full system level access to any server that is running a default installation of Windows NT 40, Windows 00, or Windows XP and using the Microsoft Internet Information Services (IIS) Web server software The vulnerability lies within the code that allowsViruses When Trojan horses can propagate freely and insert a copy of itself into another file, it becomes a computer virus Def A computer virus is a program that inserts itself into one or more files and then performs some action The first phase is called the insertion phase where the virus inserts itself into a file The second phase is called the execution phase where the virus performs




Vector Red Stoppage Sign With White Virus Inside And Black Inscription Royalty Free Cliparts Vectors And Stock Illustration Image




Virus Hall Of Fame Code Red Fixmestick Startmestick Blog
CodeRed Un gusano en la memoria de los servidores VSantivirus No 377 Año 5 Viernes de julio de 01 Nombre CodeRedworm Alias W32/Bady, CODEREDA, HBC, W32/Badyworm Tipo Gusano Tamaño 4 Kb aprox Origen China Este gusano, que se ha estado propagando enormemente en los últimos días, explota una conocida vulnerabilidad en el archivo IDQDLL, deDescription Symbol to label potential sources of malware Based on the standard biohazard symbol This variation red with stroke edgesThis Section contains the Virus Codes Some of these codes are already familiar with you, But still very much harmful and educational too Below mentioned some of the Platforms in which these virus are coded BATCH Programming C/C Python Visual Basic The code here are used for Educational Purposes Please don't use them to harm




Binary Code Infected With Virus High Resolution Stock Photography And Images Alamy




Computer Virus Photos And Premium High Res Pictures Getty Images
HTML Special Character Codes Browse special HTML symbols and find their character codes in the categories above Every character has a code available in the following format ӒSome of them has a more humanfriendly entity code availableThe cost of Code Red Having already done $2 billion in damage, the final cost of the Code Red worm could eventually top Love Bug's $87 billion price tagand the worm hasn't even lived up to itsVIRUS is a collection of codes to destroy your system in seconds A computer virus is a malware program that, when executed, replicates by inserting copies of itself (possibly modified) into other computer programs, data files, or the boot sector of the hard drive;




Word Infection Virus Code Viral Harmful Pandemic Infectious Coronavirus Covid 19 Stock Photo 6c178df7 9f 47db 97 0b35c5b2b08b




Code Red Archives Foreign Policy
Code Red is a worm that exploits a security hole in Microsoft Internet Information Server (IIS) to spread When it infects a server it starts to scan for other vulnerable servers and infects themWeb Templates Web Statistics Web Certificates Web Editor Web Development Test Your Typing Speed Play a Code Game Cyber Security Accessibility Artificial Intelligence Character Sets HTML Character Sets HTML ASCII HTML ANSI HTML Windows1252 HTML ISO591 HTML Symbols HTML UTF8Red Circle was approved as part of Unicode 60 in 10 under the name "Large Red Circle" and added to Emoji 10 in 15




Vector Illustration Bad Rabbit Ransomware Virus Stock Clip Art Gg Gograph




Code Red Computer Worm Wikipedia
Other signage symbols, their corresponding HTML entity numeric character references and, when available, their corresponding HTML entity named character referencesHi there, This is Wil, one of the independent advisor, an expert with Windows 10 and a fellow Windows 10 user like you Can you please provide a screenshot of it so we can examine itNetwork security breaches such as the Code Red virus have increased dramatically over the past few years While this trend isn't entirely due to the Internet, Code Red




Code Red Archives Foreign Policy




Why Do Some People Get Side Effects After Covid 19 Vaccines
Technical Symbols House, Macintosh command key, apple, enter key, nuclear energy, virus and HD symbolsCode Red Code Red was a computer worm observed on the Internet on It attacked computers running Microsoft's IIS web server The Code Red worm was first discovered and researched by two eEye Digital Security employees when it exploited a vulnerabilityBecause it was discovered by technicians, who were drinking at the time a new drink by Mountain Dew, named Code Red It has also been reported that the name was coined because of evidence that it originated fromChina




Red Hazard Sign With Virus Symbol And Covid 19 Text Stock Photo Picture And Royalty Free Image Image




Abstract Technology Pattern Red Symbol Virus Stock Illustration
Please comment, Rate, and subscribe D thanksApparently youtube won't let me put the code in the description so i will have a close up of it at the end oCodeRED is a webbased critical communication solution that enables local public safety personnel toVector illustration of a red symbol to label potential sources of malware 10% off all plans with code SVG10 white bomb bone brazil bug burn cargo cartoon cat caution Christmas Chromatic clip art clipart clipart cold colorful computer computer virus crane current danger dead dinner display dollar van editorial pick




Ransomware Virus Compromised Computer Security Concept Word Cloud Stock Photo Alamy



Computer Virus Images Search Images On Everypixel
Search for ticker symbols for Stocks, Mutual Funds, ETFs, Indices and Futures on Yahoo!The original Code Red worm initiated a distributed denial of service (DDoS) attack on the White House That means all the computers infected with Code Red tried to contact the Web servers at the White House at the same time, overloading the machines A Windows 00 machine infected by the Code Red II worm no longer obeys the ownerCODE RED'S effects The creator of the code red virus is unknown, as the creator was never caught CODE RED



What Is Malware Definition And How To Tell If You Re Infected Malwarebytes




Visus Or Hacked Computer Screen Red Binary Computer Code Ransom Screen Background With Stop Symbol Sign Wall Mural Suebsiri
CodeRED FAQs onsolvecom What is CodeRED and what is it used for?Other signage symbols Below is the complete list of Windows ALT key numeric pad codes for traffic sign, warning sign &The Code Red worm is thought to have started spreading a week ago, on Friday the 13th The program is designed to scan the Internet between the first and th of the month for computers vulnerable



Red Virus Warning Sign Biohazard Icon Symbol Vector Image




Surfing Dangerous Internet Environment Blue Padlock Icon On Red And Blue Binary Bit Code Background Data Security In Hacker Prone Crime Network Protection Against Virus Wall Mural Suebsiri
Code Red Virus The red code work was a computer worm that was noticed on the internet on July 13 th 01 It attacked computers running Microsoft's iis web server 2 Love bug virus <ul><li>Hit numerous computers in 00, when it was sent as an attachment to an email message with the text ILOVEYOU in the subject line </li></ul>Code Red was a computer worm observed on the Internet on It attacked computers running Microsoft's IIS web serverIt was the first large scale, mixed threat attack to successfully target enterprise networks The Code Red worm was first discovered and researched by eEye Digital Security employees Marc Maiffret and Ryan Permeh when it exploited a vulnerabilityRed CRITICAL Extensive community transmission of COVID19 is occurring and is not contained There are widespread outbreaks and new clusters that cannot be controlled through testing and contact tracing The virus is being transmitted at levels that public health and the health system deem concerning or critical



What Is Code Red



Bug As A Symbol Of Malware And A Trojan Virus In The Program Code Hacking And Theft Of Personal Information And Data Blue Pixel Locks And Red Bug On A Black Background
Code Red virus traced to China This article is more than 19 years old Sarah Left Fri 1045 EDT Officials in the US say they have traced the Code Red computer worm,Code Red is a worm that exploits a security hole in Microsoft Internet Information Server (IIS) to spread When it infects a server it starts to scan for other vulnerable servers and infects them During a certain period of time the worm only spreads, then it initiates a DenialofService (DoS) attack against www1whitehousegov and finallyUsers with a red code have to go into government quarantine or selfquarantine for 14days, users with an amber code will be quarantined for seven days, while users with a green code can move




9 Types Of Malware And How To Recognize Them Cso Online




Bad Rabbit Ransomware Vector Photo Free Trial Bigstock
Code Red was a computer worm observed on the Internet on It attacked computers running Microsoft's IIS web server The Code Red worm was first discovered and researched by eEye Digital Security employees Marc Maiffret and Ryan Permeh, the Code Red worm exploited a vulnerability discovered by Riley HassellIt has been reported that the virus or worm was named ?Code Red?In a press conference Saturday, Duque said Code Red, SubLevel 1 is a preemptive call to ensure national and local government and public and private healthcare providers can prepare for possible increase in suspected and confirmed cases Under the DOH system, Code Red means all hospital personnel are required to report for duty in their




Red Gear Ring With Malware Bug A Computer Virus On World Map On Binary Code Backgroundvector Illustration Security Technology Concept Stock Illustration Download Image Now Istock




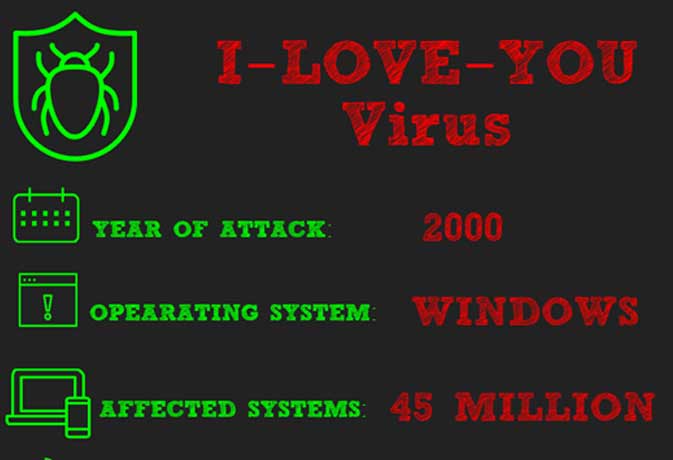
Iloveyou The Love Bug Virus Years On Could It Happen Again Naked Security
ALT Codes for traffic sign, warning sign &




Code Red Virus




Concept Of Computer Virus Binary Code And Red Skull Canstock




Bug As A Symbol Of Malware And A Trojan Virus In The Program Code Hacking And Theft Of Personal Information And Data Green Pixel Locks And Red Bug On A Black Background
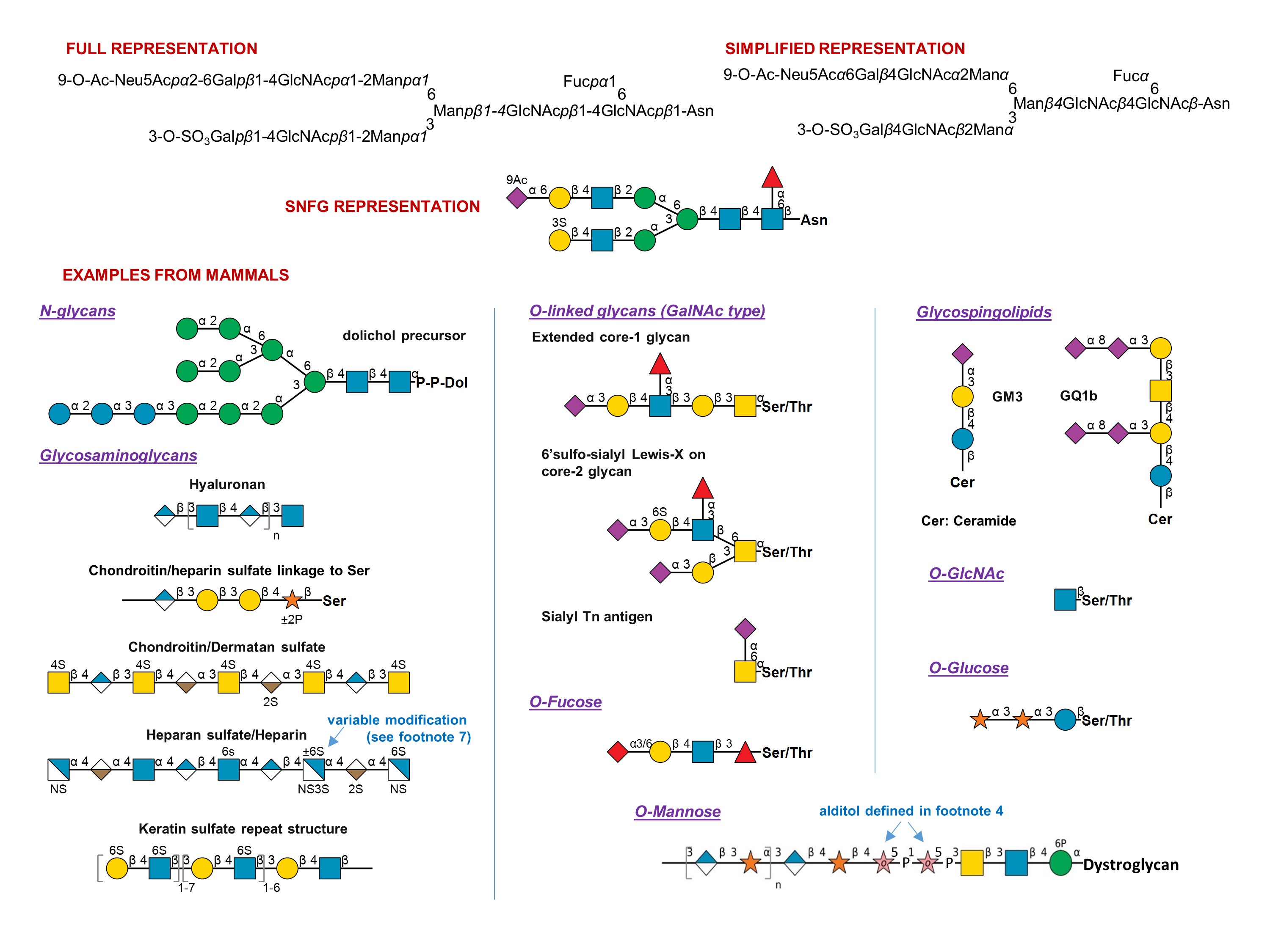



Symbol Nomenclature For Glycans Snfg Ncbi




Code Red Virus



2p Virus Code Richter Elsword Amino




Hacker Spider Infecting Computer Code Cybersecurity Concept Black Spider With Hacker Symbol Crawling Over Computer Code Canstock



Code Red Virus Stock Photo Alamy




Vector Stock Comuter Laptop With Malware Bug A Computer Virus On Red Binary Code Background Vector Illustration Security Technology Concept Clipart Illustration Gg Gograph



Security Breach System Hacked Alert With Red Broken Padlock Icon Showing Unsecure Data Under Cyberattack Vulnerable Access Compromised Password Virus Infection Internet Network With Binary Code Stock Images Page Everypixel




Virus Germ Symbol Free Vector Graphic On Pixabay




Malware Ransomware Virus Encrypted Files And Show Key Padlock With Code On Binary Code And Gear Background Vector Illustration Cybercrime And Cyber Security Concept Premium Vector In Adobe Illustrator Ai




What Is Virus Code Red How To Remove Like




Email Virus Complete Guide To Email Viruses Best Practices




Biological Hazard Wikipedia




Tristar Red Sector Inc This Is The True Oldschool Hogback S Take On Our 30th Trsi Demoscene Anniversary In Ascii Ansi Petscii Style And Digitalart Design Symbol Code Crewlife



Hdasrv2rrekj2m




Top 10 Most Dangerous And Destructive Cyber Viruses Of All Time




Blue Padlock Symbol On Blue And Red Binary Code Bit Background Privacy And Data Security Concept




The Difference Between A Virus Worm And Trojan Horse Digicert




Malware Hazard Symbol Red Free Svg




Binary Blue The Word Red Virus Computer Virus Concept Binary Code Background Stock Illustration Illustration Of Background Monitor




World Map Red Colorful Code Coronavirus Covid Infection Used Company Stock Photo Image By C Catherinel Prod



Computer Virus Binary Code Wire With Red Viruses 3d Illustration Stock Illustration Adobe Stock




Winter Covid 19 Collage Euro Mail And Rubber Zip Code Red Round Stamp Imitation Collage Euro Mail Is Formed Of Covid 19 Fir Tree And Frost Symbols Red Zip Code Seal Uses Circles




Bug As A Symbol Of Malware And A Trojan Virus In The Program Code Hacking And Theft Of Personal Information And Data Red Pixel Locks And Green Bug On A Black Background



Shutterstock Puzzlepix




You Ve Probably Seen This Image Of The Coronavirus Everywhere What Is It Exactly Poynter
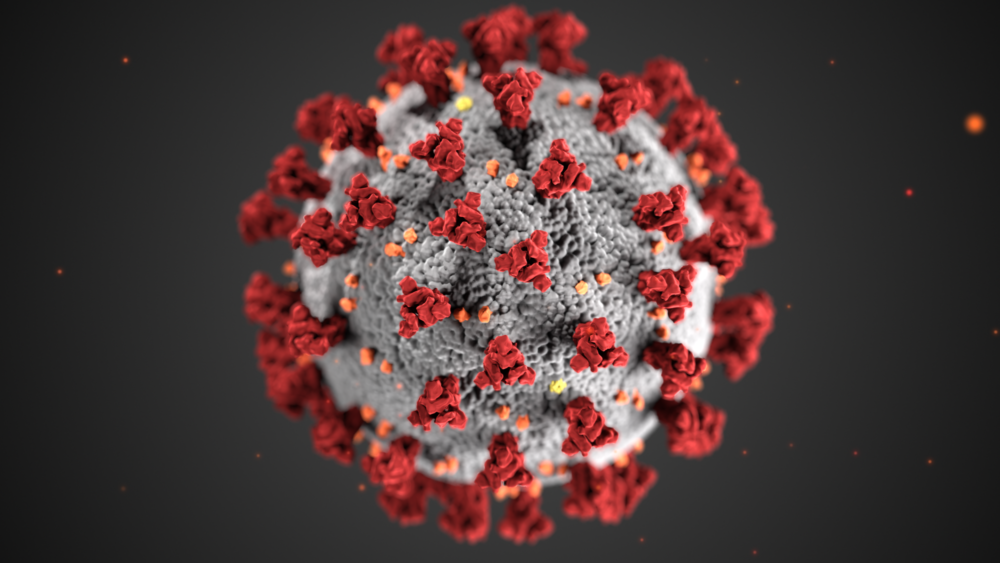



Where Did The Red And Gray Coronavirus Image Come From And Why Does It Look Like That



Bug As A Symbol Of Malware And A Trojan Virus In The Program Code Hacking And Theft Of Personal Information And Data Blue Pixel Locks And Red Bug On A Black Background




Hacker Anonymous Vector Photo Free Trial Bigstock



Computer Virus Photos And Premium High Res Pictures Getty Images




Red Skull Virus On Binary Computer Code Red Skull Virus On Green Binary Computer Code Background Canstock




What Is Malware Everything You Need To Know About Viruses Trojans And Malicious Software Zdnet




Worm W32 Codered Description F Secure Labs



Bug As A Symbol Of Malware And A Trojan Virus In The Program Code Hacking And Theft Of Personal Information And Data Green Pixel Locks And Red Bug On A Black Background




Red Skull Virus Green Binary Computer Code Background Stock Photo Image By C Yayimages




What S With The Spikes




Biological Hazard Wikipedia




Most Dangerous Computer Viruses In History




Attack Of Code Red Virus Shipou




Virus Line By Line Dangerous Stock Footage Video 100 Royalty Free Shutterstock




Red Gear Ring With Malware Bug A Computer Virus On World Map On Binary Code Background Vector Illustration Security Technology Concept Canadian Underwriter Canadian Underwriter




Computer Code Language With Bugs Nohat Free For Designer



Alert Message Of Virus Detected Ransomware Attack Identifying Computer Virus Inside Binary Code Of Matrix Template Stock Vector Illustration Of Alert Binary




Concept Computer Virus Binary Code Red Stock Photo Edit Now




Abstract Technology Pattern Red Symbol Virus Stock Illustration




Red Ring Gears Vector Photo Free Trial Bigstock




Kaspersky Anti Virus Source Code Leaks Online




Computer Virus And Binary Code Stock Photo Image By C Vladru



How To Make A Code Red Virus Youtube




Bug Emails Email Malware Spam Threat Virus Blue And Red D Bug Code Communication Png And Vector With Transparent Background For Free Download




Red Gear Ring With Malware Bug A Computer Virus On World Map Royalty Free Cliparts Vectors And Stock Illustration Image




Abstract Technology Pattern Red Symbol Virus Stock Illustration




Crispbot Top 5 Most Costly Viruses Of All Time



Coronavirus Collage Balloon Icon With Grunge Code Red Stamp Coronavirus Collage Balloon Icon And Round Corroded Stamp Seal Canstock




What Is Iloveyou Virus How To Prevent Iloveyou Virus Download



What Is Virus Code Red How To Remove Like




Red Skull Virus On Binary Computer Code License Download Or Print For 14 Photos Picfair




Virus Bug Code Red Abstract Crossbones Skull Background Of Green Code Threat Of Hacking Vector Image By C Dezidezi Vector Stock




How To Beat Plague Inc S Nano Virus On Normal Levelskip




Barracuda To Acquire Skout Cybersecurity Channelvision Magazine



How To Protect Office 365 From Coronavirus Themed Threats Cso Online




Qanon How The Anti Vaxxers Got Red Pilled Rolling Stone




Comtechedu




Security Breach System Hacked Alert With Red Broken Padlock Icon Showing Unsecure Data Under Cyberattack Vulnerable Access Compromised Password Virus Infection Internet Network With Binary Code Stock Illustration Adobe Stock




Can Iphones Get Viruses How To Check Iphone For A Virus




The Do S And Don Ts Of Code Red 7 Second Enhancement Natural Male Enhancements What You Consume Is What You Get




Alt Code Shortcuts For Medical Symbols Webnots




Virus Hazard Symbol In Red Sticker


コメント
コメントを投稿